The SolarWinds hackers are backed by Russia. They proceeded by sending messages to government employees via LinkedIn. People who visited the link on their iPhone were redirected to a malicious domain that checked whether the device was authentic. After multiple checks, the CVE-2021-1879 exploit was downloaded, which allowed to bypass certain security measures.
Google's Threat Analysis team explained the state of affairs in a report Wednesday. This team deals with all kinds of threats, regardless of platform. According to Google, the exploit disabled so-called Same-Origin-Policy protections, which normally prevent malicious scripts from collecting data. The hackers were then able to collect data from Google, Microsoft, LinkedIn, Facebook, Yahoo and other applications, and then send it to the attackers. The victim had to have a session open on the website in question to successfully collect data, Maddie Stone and Clement Lecigne explain in their report.
The exploit targeted iOS versions 12.4 through 13.7. Browsers using Site Isolation features such as Chrome and Firefox were not sensitive to this.
The team that carried out the attacks would be called Nobelium. This is the same team that ran the SolarWinds hack in 2019. Later, Nobelium also launched attacks on the United States Agency for International Development.
For ordinary users, the exploit poses no immediate threat unless you are a government employee, running an older iOS version, and have message links in LinkedIn clicked. The attacks were aimed at government employees. Apple resolved the issue in March 2021.

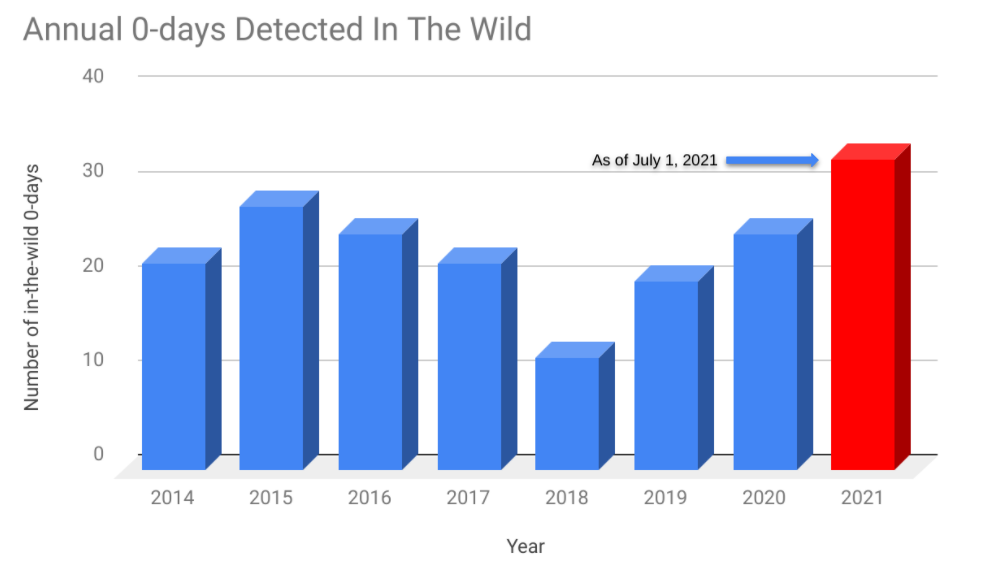
It is true that zero-days are very common in recent times. The Google researchers even speak of a “recent explosion” in the first half of this year. The group found more than 33 zero-day exploits, much more than in 2020. The fact that more are being discovered also means that the researchers are better able to track them down. In addition, more and more protections are being introduced into software, making multiple exploits possible to break in.

