AMD's Secure Encrypted Virtualization (SEV) apparently still has gaps, as German researchers found out. They line up in publications of the last few months, in which problems with AMD's SEV were also always pointed out. Firmware should not be able to close the gap. Assuming: computer access.
Research results of the TU Berlin
In May of this year AMD had already recognized the research on the problems with SEV of the Technical University of Munich and the University of Lübeck, now the Technical University of Berlin is stepping up and is shooting in the same direction with the paper “One Glitch to Rule Them All” (PDF) . All Epyc processors that support SEV are affected. In this case, however, a firmware update should not be able to fix the gap so quickly because the cause lies at the hardware level. The researchers are therefore making direct recommendations for the “next generation of Epyc processors”.
The attacks do not rely on firmware issues and can not be easily mitigated. Hence, we pro-posed mitigations for future AMD Epyc CPUs. Nevertheless, to the best of our knowledge, all currently available CPUs that support SEV are susceptible to the presented attacks.
After all, in order to exploit the gap, access to the system is required, although the exploitation should then be relatively easy, according to the analysis. Malicious administrators, as AMD recently called them, could therefore implement the attack in data centers or with other server access without any problems.
Attack using manipulated voltage
Via a so-called voltage fault injection, i.e. a changed voltage that belongs to the well-known side-channel attack variants, parameters can be changed that, for example, allow the chip to misinterpret information or even skip it completely. The chip or its firmware is secure per se, but this security can be undermined by the external manipulation of voltages: In this case, the secure firmware of the SEV is exchanged for a manipulated one, which enables attacks by the decryption of the memory for a supposedly secure VM . Again, access to the system is not even necessary because the secret keys of the CPUs linked to the CPU can be read.
The researchers conclude: AMD's SEV has not yet been able to protect confidential data in cloud environments from “insider attacks” such as criminal administrators.
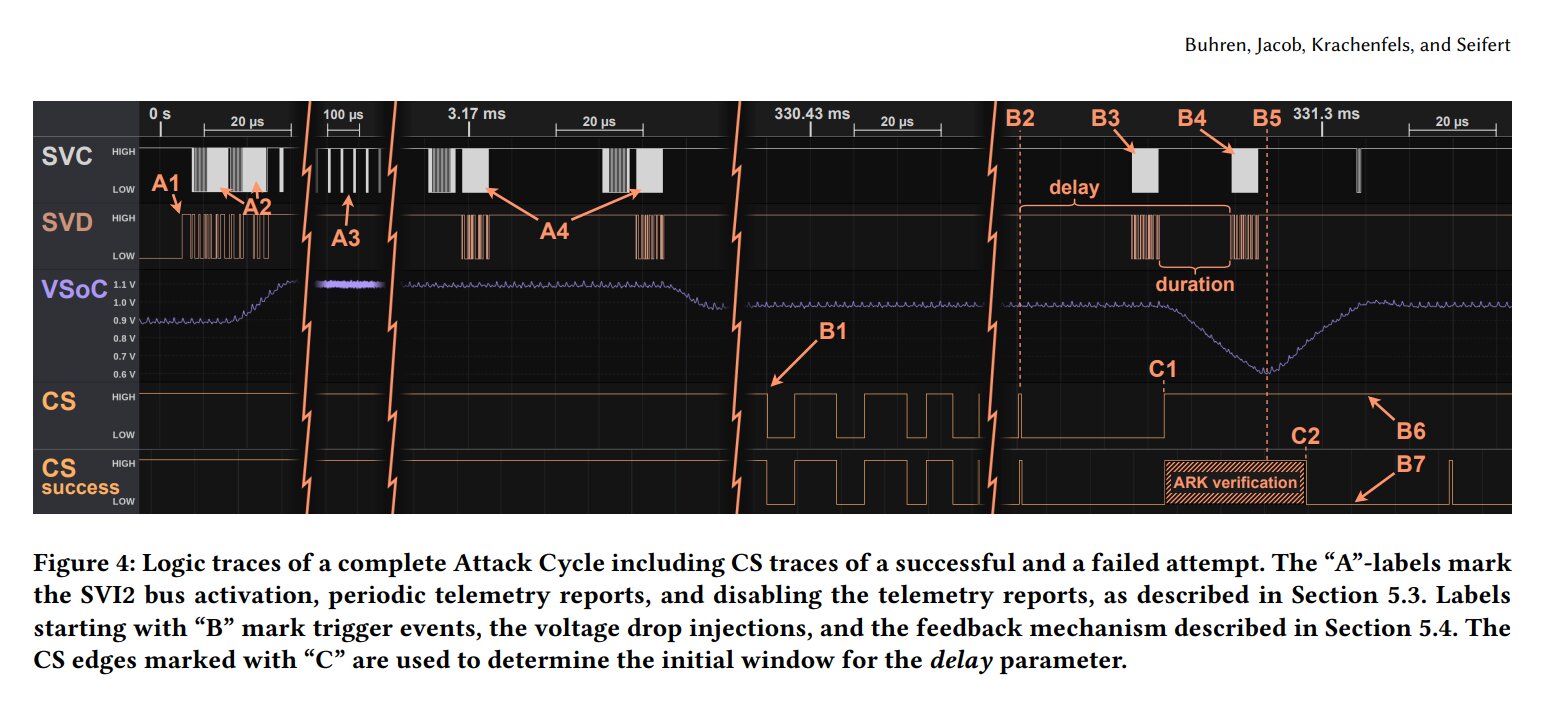 Attack on AMD's SEV in Epyc CPUs (Image: Buhren et al.)
Attack on AMD's SEV in Epyc CPUs (Image: Buhren et al.) The problems of SEV and the attackers' approach are similar to what regularly kills Intel's SGX security feature. In the end, problems were often triggered there by changing tensions. Corresponding parallels are therefore often drawn in the analysis: The researchers do not (yet) say that AMD's SEV is now developing into “AMD's SGX”.
That AMDs It was expected that hardware would come into the focus of security experts again as it became more widespread in the market. AMD declared years ago that no CPU is ever error-free.
AMD has not yet confirmed the new work by the German researchers. Just yesterday, however, AMD recognized other problems with SEV that were based on initial analyzes last year. It will be presented at a conference in August. For this problem, AMD already has a BIOS update ready at least for Milan server processors, with AGESA MilanPI-SP3_1.0.0.5 or higher the customer is covered.